What are SSH Keys ?
SSH Keys are a type of secure shell key used to authenticate a user and provide secure access to a computer or network. They consist of two parts: a public key and a private key. The public key is shared with the remote server for authentication, while the private key is kept secret by the user. SSH Keys are an important part of any security system and must be managed properly in order to ensure secure access.
What is RSA?
RSA encryption is one of the most popular and secure methods of data encryption. It is based on a mathematical algorithm that uses two prime numbers to create a public key for secure data transmission. RSA algorithm has been used for decades in various applications and can be used to protect confidential information from being intercepted or altered during transmission.
RSA encryption is considered one of the strongest forms of data security available today due to its ability to securely encrypt and decrypt messages, as well as its resistance to brute-force attacks. This makes it an ideal choice for organizations that need to protect sensitive data, such as financial information or medical records.
1. How to Generate SSH Key in Linux
To create a private key and matching public key for authentication, use the ssh-keygen command. By default, your private and public keys are saved in your ~/.ssh/id_rsa and ~/.ssh/id_rsa.pub files, respectively.
# ssh-keygen
Example with output :
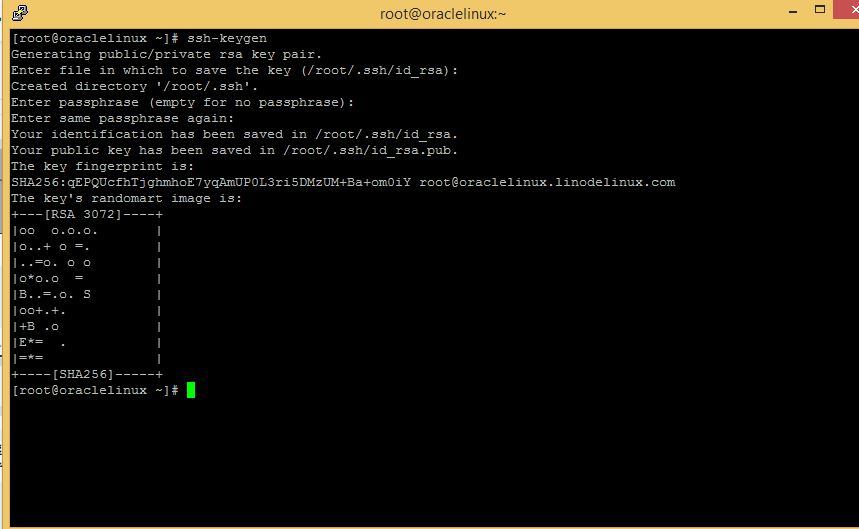
If you do not specify a passphrase when ssh-keygen prompts you, the generated private key is not protected. In this case, anyone with your private key file could use it for authentication. If you set a passphrase, then you will need to enter that passphrase when you use the private key for authentication.
Sharing the Public Key
Before key-based authentication can be used, the public key needs to be copied to the
destination system. The ssh-copy-id command copies the public key of the SSH keypair to the
destination system. If you omit the path to the public key file while running ssh-copy-id, it uses
the default /home/user/.ssh/id_rsa.p
2. Copying the SSH key to the Host :
# ssh-copy-id username@remotehost
3. Log in to the Server
After successfully copying the SSH key to the host, we can log in without password
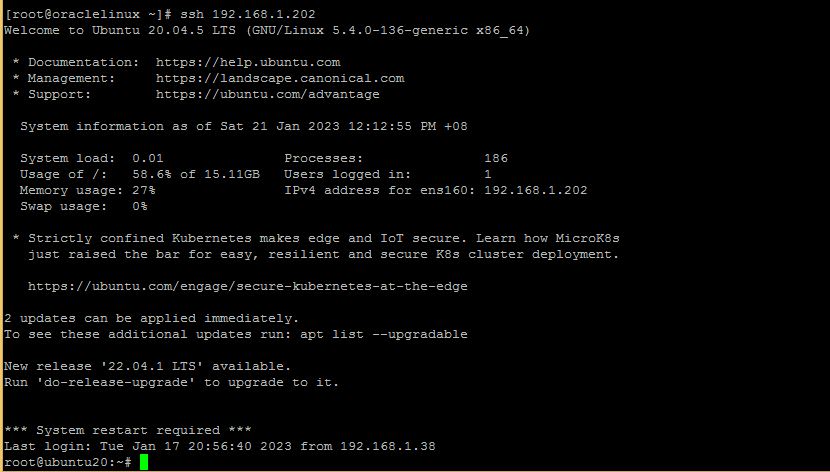
# ssh username@remotehost
Example :
Conclusion:
SSH keys are a crucial part of any secure system and taking the necessary steps to secure your SSH Keys is crucial for maximum protection. Without taking the necessary steps to properly secure them, your system will be vulnerable to malicious actors. This will ensure that your SSH keys remain secure and protected from unauthorized access.
Learn more on How to Setup SSH Login Without Password in Linux